In our interconnected digital world, where personal and business data flow seamlessly across global networks, preventing unauthorized data access has become a paramount concern for individuals and organizations alike. Imagine the repercussions of sensitive data falling into the wrong hands—financial loss, reputational damage, and invasion of privacy. Can we afford to be complacent when such profound risks are lurking just a click away? The answer is a resounding no. It’s time to actively safeguard our digital assets and erect formidable barriers against unauthorized access.
Read Now : Enterprise-level Distributed Ledger Applications
The Unseen Threats Lurking in the Shadows
In today’s technological landscape, preventing unauthorized data access is no small feat. Cyber attackers are continuously evolving their tactics to exploit vulnerabilities and penetrate digitally safeguarded walls. These breaches can result in devastating financial losses and irreparable damage to brand reputation. Protecting sensitive information is not just about installing antivirus software; it’s about building a robust defense-in-depth strategy. This involves using encryption, multi-factor authentication, and diligent monitoring of network traffic. Moreover, regular audits and updates are vital in identifying potential weaknesses that could lead to unauthorized data access. The digital world is fraught with dangers, but you have the power to fight back and protect what’s rightfully yours.
Guarding Your Digital Fortresses
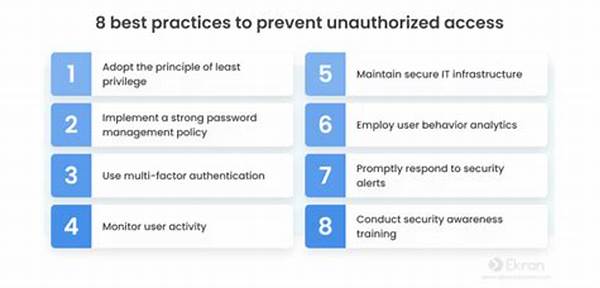
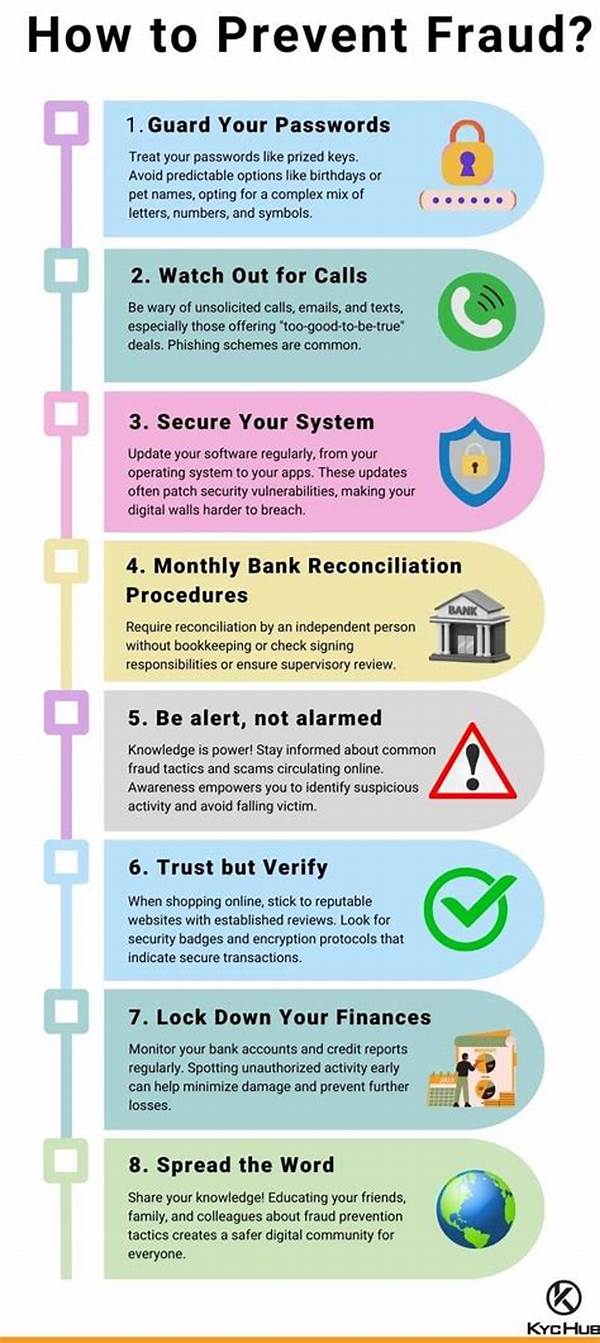
1. Implement Strong Password Policies: One fundamental step in preventing unauthorized data access is enforcing strong password protocols. Encourage the use of complex passwords that include a mix of characters, numbers, and symbols to enhance security.
2. Adopt Multi-Factor Authentication: Elevate your security game by implementing multi-factor authentication, adding an extra layer of defense against intruders. This simple yet effective step can significantly reduce the likelihood of unauthorized data access.
3. Regular Software Updates: Keep software up to date to patch security vulnerabilities. Effective patch management plays a crucial role in preventing unauthorized data access and ensuring systems remain secure against the latest threats.
4. Educate and Train Employees: An informed workforce is your first line of defense. Training employees on recognizing phishing attempts and adhering to security best practices is instrumental in preventing unauthorized data access.
5. Conduct Regular Security Audits: Regularly auditing your systems for vulnerabilities is crucial in preventing unauthorized data access. These assessments help identify gaps in security protocols and allow for timely countermeasures.
The Role of Encryption in Safeguarding Information
Encryption serves as a powerful tool in the fight against unauthorized data access. It converts sensitive data into a code that is indecipherable without the correct decryption key. This process ensures that even if cybercriminals manage to capture data, they cannot make any sense of it. As organizations increasingly rely on digital communication and data storage, implementing encryption is more crucial than ever. Encrypting data both at rest and during transmission safeguards it from unauthorized prying eyes. It’s a shield that upholds the integrity and confidentiality of information, providing peace of mind in an era marked by frequent digital breaches.
Investing in robust encryption solutions is an essential strategy for businesses determined to protect their data from cyber threats. Beyond just technical implementation, encryption demands ongoing commitment to security, including key management practices and compliance with industry standards. This proactive stance not only deters unauthorized data access but also demonstrates a commitment to safeguarding customer trust and business continuity. Organizations must understand that protecting data is not a one-off act but an ongoing process requiring vigilance and adaptability.
Practical Steps for Businesses in Preventing Unauthorized Data Access
1. Develop a Comprehensive Security Policy: Preventing unauthorized data access begins with a well-documented security policy outlining acceptable use, response protocols, and employee responsibilities regarding data security.
2. Utilize Advanced Monitoring Tools: Employ cutting-edge monitoring solutions to detect unauthorized access attempts in real time. These tools can alert your team to potential breaches and enable swift action.
3. Restrict Access Based on Necessity: Limit data access based on roles and responsibilities. By adhering to the principle of least privilege, you reduce the risk of unauthorized data access.
4. Engage in Regular Cybersecurity Training: Update your employees regularly on the latest security threats and measures. Awareness and preparedness play a formidable role in preventing unauthorized data access.
5. Implement Network Segmentation: Isolating sensitive data within segments of your network acts as an additional barrier, preventing unauthorized users from easily accessing critical information.
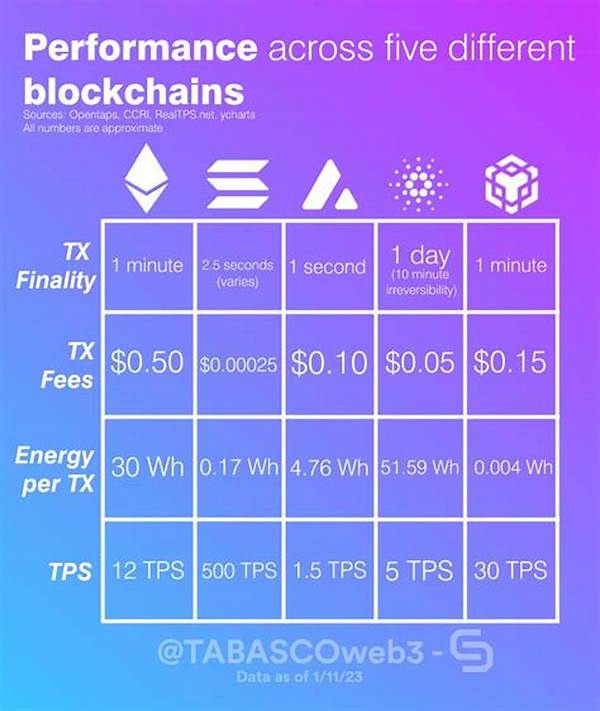
Read Now : Solana Blockchain Performance Comparison
6. Plan for Incident Response: Preparedness in responding to security incidents is as crucial as preventive measures. Develop and regularly update your incident response plan to mitigate the impact of unauthorized data access.
7. Foster a Security-First Culture: Cultivate an environment where data security is prioritized among all stakeholders, encouraging a collective effort in preventing unauthorized data access.
8. Vet Third-Party Vendors Thoroughly: Any external service provider should meet rigorous security standards to avoid vulnerabilities that could lead to unauthorized data access.
9. Constantly Evaluate Your Security Posture: Regular assessments of your security strategies ensure they are effective and aligned with evolving threats.
10. Stay Informed of Cyber Trends: Keeping abreast of emerging cyber threats and vulnerabilities is crucial to adapting your strategies for preventing unauthorized data access.
Building a Security Framework for the Future
Preventing unauthorized data access is not merely a technological challenge; it’s an organizational imperative. As digital transformations continue reshaping industries, the significance of a robust security framework cannot be overstated. Every organization, regardless of size, must embrace a proactive security stance, investing in tools and training that empower employees to be vigilant and informed. This holistic approach ensures a sustainable defense mechanism resilient against both current and future cyber threats.
Security is a journey, not a destination. Organizations must continuously refine their security strategies to anticipate emerging challenges. The stakes are high, but with a dedicated focus on preventing unauthorized data access, businesses can turn the tide against cyber adversaries. A secure digital environment is not merely an asset; it is a foundation upon which innovation and trust are built. Embracing a culture of vigilance, adaptation, and foresight is vital for long-term success, ensuring that data protection remains robust and dynamic.
Key Elements in Strengthening Data Security
Prevention of unauthorized data access hinges on a comprehensive strategy combining technological solutions and organizational practices. A robust security posture integrates state-of-the-art technologies, such as AI-driven threat detection, with fundamental organizational changes, including enhanced training and development of incident response plans. This dual approach addresses both external threats and internal vulnerabilities, ensuring a resilient defense system capable of thwarting a wide range of cyber threats.
Organizations must regularly evaluate and update their security frameworks to reflect changes in the threat landscape and technological advancements. Effective communication and alignment across all levels of the organization are critical to maintaining security protocols. Adopting an agile mindset towards data security enables faster responses and adaptability, ensuring that the organization can effectively manage and mitigate risks associated with unauthorized data access.
Summary: Taking Charge of Your Data Security
Preventing unauthorized data access is a complex yet crucial endeavor for any organization operating in today’s digital age. As cyber threats become more sophisticated, the need for comprehensive security measures intensifies. This effort encompasses both technological defenses and proactive organizational strategies that empower individuals to mitigate potential risks.
Building a robust security culture requires ongoing investment in education, resources, and technology. By fostering awareness and accountability, organizations lay down the foundation for a secure environment. A proactive stance combined with vigilance and a commitment to continuous improvement will play a critical role in safeguarding valuable data assets from unauthorized access. By prioritizing data security today, you not only protect your organization but also pave the way for a secure and innovative future.